Sync Without Leaks: Private Messaging Across Phone, Tablet, and Desktop
Your messages appear on all your devices. The privacy aspect gets murky here. Texting someone from your phone creates one connection between two people. Spread the conversation across your laptop, tablet, and desktop. Things get messy fast. Most people never consider the problems.
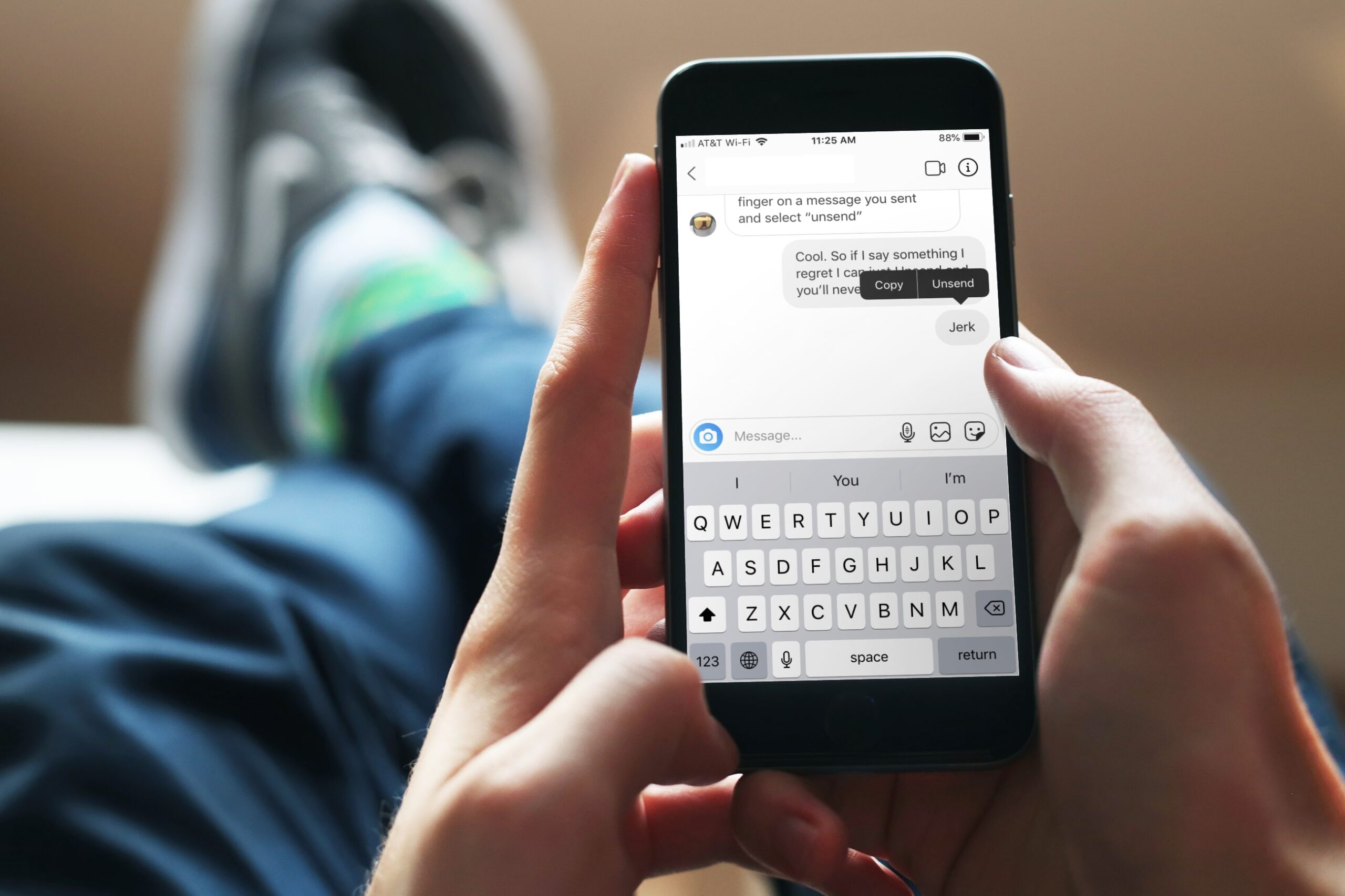
Architecture That Creates Problems
Messaging walked a straight line once—one sender's words traveling directly to one receiver's eyes, a closed circuit with no eavesdroppers allowed.
Multiple devices shatter the elegant simplicity like a hammer through glass. You're having this bizarre conversation with yourself across five different screens, each one frantically unlocking everything and racing to catch up with the others—a chaotic juggling act nobody asked for.
Companies funnel everything into one massive digital warehouse. All your devices come shopping there for what they need. Users love this approach—messages bloom across their screens without any fuss. You've created this towering stockpile of locked information. Concentration like hanging a neon sign saying “valuable data here” for anyone with wrong intentions.
Signal carved out a different path entirely. Your phone sits at the center. Main hub for everything. Your laptop has to shake hands directly with your phone. Signal stays out of the transaction. Chat history never piles up in their infrastructure.
Your phone needs to be reachable for anything else to work properly. People expect their messages to just appear everywhere—poof, digital fairy dust style—they end up disappointed.
The centralized approach dominates the market. Nobody tolerates hearing “sorry, one device was offline so your messages evaporated into the digital ether.”
It delivers on promises most of the time. Companies juggle locked information according to whatever playbook they've written for themselves. They publish statements about their record-keeping practices.
How The Privacy Part Works?
Companies running these services can't peek into what you're saying—the entire selling point. Messages get locked up tight on your screen.
They stay locked. They reach whoever you're talking to. No stops along the way for someone to jimmy them open and take a look. Your own collection of devices each need their own key to unlock things. Passing those keys around safely gets complicated fast.
Sloppy setups just shuttle keys over the internet wrapped in password protection. Stuffing your house key into fake garden rocks—nobody's fooled.
The folks figuring out encryption came up with something far more elegant. Your devices make two paired things—one gets thrown out there for everyone to see, the other stays hidden. Your devices trade the public ones around and each works out a secret independently. Anyone listening in can't figure out how to recreate what just happened.
Fresh keys spring to life with each message passing through—constantly reborn like phoenixes from digital ashes. Someone manages to snatch one?
Snapshot has limited value beyond a single moment. They bloom and wither in rapid succession, each one alive just long enough to protect a single exchange before fading away, containing any security breach to a sliver of vulnerability.
The Stuff Around Messages
Your messages might be sealed up tighter than a drum. Everything surrounding them still sketches a surprisingly detailed portrait of your life.
Who you chat with, when conversations light up your screen, how often they occur, your location—these patterns map out relationships, carve routines into stone, chronicle shifts in behavior. Observers often mine more gold from surrounding data than from actual words.
Platforms tear apart sender identity from the message itself. Their routing infrastructure only knows destinations, can't draw maps of who communicates with whom.
Information genuinely doesn't live in their systems. Burns more computational fuel, pushes operating costs higher. The chasm separating real privacy from performative privacy lives here.
Verifying your identity unfolds every time you crack open the app on something different. Careless implementation leaves breadcrumb trails documenting when and from which specific device you accessed the service.
Smarter approaches deploy temporary credentials vanishing immediately after confirming your identity. Nothing left behind to trace.

App Choices
The WhatsApp vs Signal security and privacy debate crystallizes these architectural trade-offs. WhatsApp borrowed Signal's method wholesale. The underlying technology does the job admirably. Lives inside Meta's sprawling digital kingdom though.
Questions bubble up about surveillance practices, how it meshes with Meta's advertising engine, whether privacy commitments can weather revenue pressures—these concerns don't just evaporate.
Signal emerged from intentional design decisions. Nonprofit structure built around collecting the bare minimum. The codebase sits in plain view for anyone to inspect, the organizational architecture has antibodies against monetization temptations, the platform hoards barely any user data by deliberate choice.
You sacrifice features and network effects. The platform fundamentally can't sell out its principles without destroying its entire reason for existing.
Telegram went down a completely different road. Regular chats skip the heavy-duty protection—only their “secret chats” get it. Those specific chats stick to whatever device you started them on, refusing to show up anywhere else.
They went for maximum features over maximum security, swapping heavy fortress walls for something lighter and more flexible. Most people don't need military-grade protection for everyday conversations.
Local Storage
Messages touch down on your device and nestle into storage in a completely different universe from network protections. Someone makes off with your laptop or successfully plants something malicious on it. Your entire chat archive sits exposed like an open book. Messages traveled through secure tunnels. Now they're just resting there.
Stored information gets wrapped in protection using codes pulled from your PIN or something baked into your hardware. Works beautifully. Your screen stays dark. Leave it glowing and everything becomes readable. Malicious code doesn't need to crack anything. Information already sits there waiting.
Basic password schemes can be attacked offline. Someone walks away with your database files. Specialized chips in phones or cordoned-off areas in computers store codes in hardware built to fight off physical tampering. Even with complete takeover, extracting those codes becomes exponentially harder.
Device Management
Connecting something new usually involves one screen flashing a code. The other captures it. The phone you normally carry displays what's necessary, the new device scans it. Reading a barcode. They complete their dance without anything sensitive traveling over the internet.
Account recovery throws sand in the gears. You lose access to everything and desperately need a way back in. Any backdoor potentially compromises what you've built. Platforms either refuse recovery altogether—lose your hardware, wave goodbye to your history—or they weave in PIN systems and trusted contact networks. Fresh failure modes get introduced.
Reality Versus Whiteboards
Systems look pristine on whiteboards. Engineers build them and they crumble. Bugs nest in software. Spots break, hide in how things run. You start connecting different pieces. Problems breed like rabbits. Any of these flaws can flatten what should theoretically work.
Open-source code lets researchers examine how everything works before criminals find the vulnerabilities. Closed code demands faith that internal teams found every flaw. History repeatedly demonstrates how trust crumbles—a pattern of disappointment playing out with remarkable consistency.
Real commitment shows through actions, not glossy marketing language. Security experts circling like hawks. Programs dangling cash rewards for anyone spotting the cracks. Honest conversations when walls come tumbling down. Doing the hard work or putting on a show—you can tell the difference pretty fast.
Threats morph and mutate like organisms under evolutionary pressure—what worked yesterday becomes obsolete tomorrow. Protection strategies have grown and adapted in response, an arms race running since the first person decided to hide a message.
This back-and-forth has existed since the beginning. Platforms thriving grasp something fundamental about this domain. Security looks great in theory but confuses people in practice. Ends up protecting nobody. You need something tough enough to stop determined criminals.
Simple enough that someone checking messages over morning coffee doesn't accidentally break everything. Being totally secure. Being usable. The really hard problems live right in the middle, the ones keeping security experts up at night trying to figure out.

Jim's passion for Apple products ignited in 2007 when Steve Jobs introduced the first iPhone. This was a canon event in his life. Noticing a lack of iPad-focused content that is easy to understand even for “tech-noob”, he decided to create Tabletmonkeys in 2011.
Jim continues to share his expertise and passion for tablets, helping his audience as much as he can with his motto “One Swipe at a Time!”
